Quantum computers are no longer science-fiction—they’re on real hardware roadmaps. A 2025 study from the Q-Day research group estimates that about 1,400 fault-tolerant qubits can break an RSA-2048 key in just five days.
That looming “Q-Day” forces a choice: keep trusting blockchains secured by classical math, or shift to encryption grounded in quantum physics. Over the next pages, we’ll compare both paths and give you a clear, quarter-by-quarter plan to future-proof your data.
How quantum cryptography works
Quantum cryptography and blockchain security together form the foundation for future-proofing data against Q-Day.
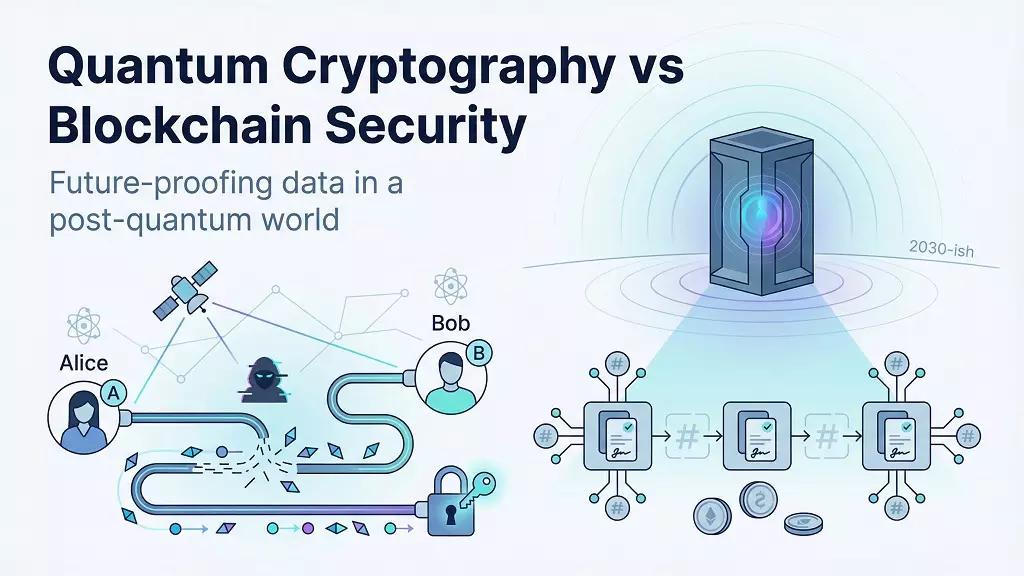
Quantum cryptography converts the laws of physics into a security service. In its flagship protocol, quantum key distribution (QKD), Alice encodes each bit of a secret key onto the polarization of a single photon and sends it to Bob through fiber or free-space optics.
If Eve intercepts even one photon, the measurement collapses the quantum state, flips its value, and Bob’s error check exposes the intrusion immediately.
For a broader perspective on how quantum technologies are already shaping real-world systems, Decipherzone explains current trends in quantum software development.
Real-world performance already meets metro-network needs. ID Quantique and the University of Geneva generated 64 Mb/s of secret key over 10 km of fiber and 3 Mb/s over 102 km.
For long haul, research from the University of Science and Technology of China has driven secure links beyond 830 km of ultralow-loss fiber, while China’s Micius satellite shared entangled-photon keys between ground stations 1,120 km apart.
Beyond key delivery, quantum devices also work as true random-number generators, sampling vacuum noise to create entropy no algorithm can predict. Many commercial HSMs now embed a quantum RNG to strengthen classical cryptography.
This evolution is part of a larger shift toward advanced computing models, which Decipherzone explores in its overview of the role of quantum computing in modern applications.
In short, quantum cryptography detects eavesdropping by design, scales from data-center corridors to continental distances, and provides provably random keys. Next, we’ll weigh those physics-level guarantees against the “math-plus-consensus” model that blockchains use today.
Quantum cryptography in plain English
Quantum key distribution (QKD) is a physics-driven way to share a secret key. Alice encodes each bit on the polarization of a single photon, sends it to Bob, and the pair run a public error check.
If an eavesdropper measures even one photon, the quantum state collapses, the error rate jumps, and the intrusion shows up instantly.
The method already works outside the lab. In 2023 researchers from ID Quantique and the University of Geneva pushed QKD to 64 Mb/s over 10 km of fiber and 3 Mb/s over 102 km, keeping the error rate below 0.4 percent.
Satellite links reach farther: China’s Micius spacecraft has swapped entangled-photon keys between ground stations more than 1,100 km apart.
Quantum tech also fixes the “weak randomness” problem. Commercial quantum random-number generators such as Quantum Dice’s APEX card generate 7.5 Gb/s of certified entropy, far faster than pseudo-random software can manage.
In short, QKD turns wiretaps into detectable noise, and quantum RNGs deliver keys no classical algorithm can predict. Together they form the backbone of quantum cryptography; next, we’ll see how they compare with the math-based defenses inside today’s blockchains.
How blockchain keeps data honest, and why quantum puts that honesty at risk
Blockchains stay tamper-proof by tying two pieces of classical cryptography to a public ledger:
-
Digital signatures (ECDSA). Only someone with the private key can authorize a transaction, and every node can verify the signature.
-
Hash links (SHA-256). Each block contains the hash of the one before it, so altering a single byte breaks the entire chain.
Decentralized consensus on top of those tools has protected about $1.7 trillion in Bitcoin value as of December 1, 2025.
For readers who want a foundational understanding of how these mechanisms work together, Decipherzone provides a clear guide to blockchain technology.
Yet the rapid pace of quantum computing research means adversaries could soon wield machines capable of undermining these classical safeguards.
Ensuring these systems remain reliable at scale requires rigorous validation, a topic Decipherzone covers in detail through its insights on blockchain testing.
Quantum algorithms threaten both pillars:
-
Shor’s algorithm could derive an ECDSA private key from its public key once hardware scales to tens of millions of fault-tolerant qubits, making signature forgery practical.
-
Grover’s algorithm would, in theory, cut SHA-256’s brute-force work factor from 2²⁵⁶ to 2¹²⁸ operations—still vast, yet a full 128-bit security drop.
A Deloitte report identifies about 4 million BTC, roughly twenty-five percent of supply, sitting in address types whose public keys are exposed, worth more than $340 billion at today’s price.

Quantum algorithms like Shor’s and Grover’s target blockchain signatures and hashes, putting exposed BTC at risk.
Project 11’s Bitcoin Risq List, which tracks addresses exposed to future quantum attacks, estimates that more than 6.2 million BTC sit in particularly high-risk categories such as long-dormant wallets and reused keys, representing over $600 billion in value as of January 2025.
Taken together, those analyses show how much “harvest-now, decrypt-later” material already exists for any adversary recording traffic ahead of Q-Day.
Quantum-capable attackers could re-sign those coins and move them before honest nodes respond.
Even modern P2PKH addresses remain safe only until the first spend reveals the key. Attackers can harvest traffic today, decrypt tomorrow, planting a long-fuse threat under any chain that fails to adopt quantum-safe algorithms.
Bottom line: blockchain consensus remains solid, yet its cryptographic locks are classical. A single forged signature, with no fifty-one percent attack required, could drain funds or shatter confidence. The next section maps the post-quantum toolkit you can deploy before that day arrives.
Post-quantum cryptography: new locks for old doors

The fastest way to blunt a quantum attack is to swap the math qubits exploit rather than rebuild an entire network. That solution arrives as post-quantum cryptography (PQC).
After eight years of public vetting, NIST finalized three Federal Information Processing Standards on August 13, 2024:
-
FIPS 203 (ML-KEM) – encryption based on CRYSTALS-Kyber
-
FIPS 204 (ML-DSA) – signatures based on CRYSTALS-Dilithium
-
FIPS 205 (SLH-DSA) – hash-based backup using SPHINCS+
In March 2025, NIST added HQC as a fourth, fallback KEM and announced plans for a Falcon-derived signature draft in 2026.
Why care? Because these algorithms run on servers, phones, and blockchains already in production, turning an upgrade into a software push:
-
Kyber-768 public key: 1,184 bytes, ciphertext: 1,088 bytes
-
Dilithium-3 signature: 3,293 bytes (about 3.2 KB) versus 64 bytes for ECDSA
Packets grow, logs swell, and wallets require a larger buffer, yet that overhead is tiny compared with a forged transaction draining a treasury in seconds.
Post-quantum standards such as Kyber, Dilithium, and SPHINCS+ act as new locks that run on today’s hardware.
Next, we will see how live blockchains fold these algorithms into production networks, and how hybrid “classical plus quantum-safe” signatures let teams migrate without breaking downstream tools.
Quantum vs blockchain: a reality check
1. Security against quantum attacks
Quantum cryptography wins confidentiality today. A single intercepted photon exposes an eavesdropper, and NIST-approved PQC schemes such as Kyber, Dilithium, and SPHINCS+ resist known quantum algorithms.
Blockchains require an upgrade. Shor’s algorithm could forge an ECDSA signature once hardware reaches about 13 million error-corrected qubits. Until a chain adopts PQC or dual signatures, an attacker needs only one forged key to steal funds.
2. Maturity and adoption
QKD networks operate in more than 60 countries and already secure an 800 km government backbone in South Korea.
Bitcoin clears about 480,000 on-chain transactions each day—roughly 5.5 TPS—and open-source stacks let teams spin up a private chain in hours. PQC libraries can ship in a sprint, whereas a continent-wide QKD mesh is a multiyear project.
3. Scope of protection
Quantum tools guard secrecy by stopping key theft. They do not record who changed a ledger entry. Blockchains broadcast every state change to thousands of nodes, preserving integrity yet exposing plaintext unless paired with encryption. Together, the two cover different columns of the CIA triad.

Quantum tools lock down confidentiality, while blockchains enforce integrity—together they close the security gaps.
4. Performance and practicality
-
Fourth-generation QKD appliances reach 64 Mb/s secret-key rate over 10 km fiber and 3 Mb/s beyond 100 km. Satellite hops span more than 1,100 km yet add latency.
-
Dilithium-3 signatures weigh about 3.3 KB, and a Kyber-768 handshake adds roughly 2.2 KB, inflating TLS packets and blockchain transactions.
-
Proof-of-Work Bitcoin averages 7 TPS; a December 2025 Solana testnet ran 50,000 TPS with less than five percent CPU uplift after replacing ECDSA with Dilithium.
5. Cost and resource intensity
Library swaps to PQC add developer time, bandwidth, and storage. A Cerberis XG QKD node lists in the high five-figure USD range per link and requires dedicated fiber or satellite capacity. Running a blockchain validator fleet is largely cap-ex neutral, but PQC migration increases block size and log storage.
Bottom line: quantum cryptography already future-proofs privacy, while PQC-hardened blockchains protect integrity. Layer them together to cover every side of the threat model.
Maturity and adoption
Quantum cryptography is real, yet still boutique. ID Quantique says its QKD hardware operates in more than 60 countries across government, telco, and research networks. In 2024, JPMorgan Chase secured a 100 Gb/s link between two data centers with QKD-derived keys.
Europe’s €90 million EuroQCI program plans to connect 27 member states by 2026. Impressive milestones, yet they cover only a few hundred links, not the public internet.
Blockchains already run at consumer scale. Bitcoin processes about 480,000 on-chain transactions per day (seven transactions per second) and supports roughly 93 million self-custody wallets.
Ethereum clears 1.6 million transactions in 24 hours, and layer-2 networks push total settled activity even higher. Open-source node software, cloud templates, and audited SDKs let a team launch a private chain in hours.
To accelerate implementation, companies can hire expert blockchain developers from Decipherzone to deploy secure, post-quantum-ready solutions.
Take-away: you can ship PQC libraries in your next sprint, whereas creating a metro-scale QKD mesh demands a multi-year budget. A smart roadmap starts with upgrading blockchain keys to post-quantum algorithms now, then adds QKD links around crown-jewel data centers as funds permit.
Scope of protection
Security teams often frame risk with the CIA triad:
-
Confidentiality – keeping data secret
-
Integrity – ensuring data cannot be altered undetected
-
Availability – keeping systems online and retrievable
Quantum cryptography, notably quantum key distribution, addresses only the first pillar. It generates keys that remain secret even from a future, unbounded adversary, yet it does not say who changed a record or whether a database entry was altered.
The NSA notes that QKD “is only a partial solution… it generates keying material for confidentiality but offers no source authentication or data-integrity guarantee.”
Blockchains focus on the second pillar. Each block carries a timestamp, a hash of the prior block, and thousands of replicas, so any unauthorized edit becomes obvious. Bitcoin’s ledger, for example, has logged more than 850 million transactions since 2009 without a confirmed rewrite.
The data inside those blocks is public by design unless users add encryption, and the signatures that secure spends remain classical.
Put simply:
-
Quantum tools lock the door against eavesdroppers.
-
Blockchains install tamper alarms throughout the house.
Paired together—post-quantum encryption for secrecy, plus a blockchain for an auditable, immutable history—you close both gaps in the threat model.
Performance and practicality
-
Fourth-generation QKD appliances reach 64 Mb/s secret-key rate over 10 km fiber and 3 Mb/s beyond 100 km. Satellite hops cover more than 1,100 km while adding round-trip latency.
-
Dilithium-3 signatures measure about 3.3 KB, and a Kyber-768 handshake adds roughly 2.2 KB, enlarging TLS packets and blockchain transactions.
-
Proof-of-Work Bitcoin averages 7 TPS. A December 2025 Solana testnet processed 50,000 TPS with less than five percent CPU uplift after swapping ECDSA for Dilithium.
Take-away: quantum links face physics-imposed bandwidth and latency limits, while blockchains face consensus-bound TPS and storage ceilings. PQC enlarges packets, yet early benchmarks show modern L1 and L2 chains absorb the overhead with modest tuning.
Cost and resource intensity
Upgrading to PQC mostly consumes developer hours, extra bandwidth, and additional storage. A Cerberis XG QKD node lists at between 70,000 and 90,000 USD per link and needs dedicated fiber or satellite capacity. Running a blockchain validator fleet remains largely capital-neutral with open-source software; however, a PQC migration increases block size and log storage, so teams should budget for roughly 30 percent more disk space and network traffic.
Industry momentum: from lab talk to live pilots
-
Standards locked in. The U.S. Commerce Secretary approved FIPS 203, 204, and 205 on August 13, 2024, finalising Kyber, Dilithium, and SPHINCS+ as the first federal post-quantum standards. A Falcon-based draft enters review in 2026.
-
Capital markets move early. On May 8, 2024, JPMorgan Chase activated a production 100 Gb/s quantum-secured link between data centres using QKD keys, forming part of its Q-CAN network.
-
Public-chain proof. December 16, 2025: Project Eleven and the Solana Foundation ran a Dilithium-signed testnet that processed 50,000 TPS with less than five percent CPU uplift on validators.
-
Continental roll-outs. Europe’s €90 million EuroQCI program closed its 2025 call with twenty-four cross-border proposals that connect the 27 EU member states through QKD satellites, fiber, and terrestrial relays.
-
Vendor ecosystem. ID Quantique ships its fourth-generation Cerberis XG platform, quoting 64 Mb/s key rate over 10 km fiber and customers in more than 60 countries.
Together these milestones confirm that quantum-safe crypto has passed the lab stage. Standards are official, banks route live money over quantum links, and a high-speed public blockchain has demonstrated post-quantum signatures in the wild.

From NIST standards to live QKD networks and PQC blockchains, quantum-safe crypto is already in production.
Action plan: nine moves to stay quantum-ready
-
Inventory your crypto footprint. Map every place that relies on RSA, ECC, or SHA-1/256—source code, backups, third-party APIs, and vendor systems. NIST IR 8547 lists discovery as “Step 0” in its migration timeline.
-
Tag long-lived secrets. Flag data that must remain private beyond 2030. NIST warns that harvest-now, decrypt-later attacks are already in progress.
-
Pilot PQC libraries in development. Insert Kyber and Dilithium test builds. Cloudflare measured less than one millisecond of extra handshake time on broadband links.
-
Design for crypto-agility. Wrap signing and key-exchange calls in versioned interfaces, allowing algorithms to be swapped without rewriting applications.
-
Roll out dual signatures. Combine ECDSA and Dilithium during transition, following guidance in NIST SP 800-208 for hash-based signatures.
-
Adopt quantum-grade randomness. Hardware QRNG chips cost roughly one US dollar at smartphone volumes, offering inexpensive entropy insurance.
-
Set internal deadlines. The US Office of Management and Budget targets January 2, 2030 for federal TLS 1.3 deployments with PQC support. Mirror that schedule: new systems run PQC only by 2027, and legacy platforms migrate by 2030.
-
Train the builders. Add “quantum-safe coding” to 2026 team objectives. NIST IR 8547 lists workforce upskilling as a critical-path item.
-
Monitor the threat radar. Track qubit milestones and public cryptanalytic results, updating this roadmap every six months.

Conclusion
Follow these nine moves, and quantum risk becomes just another security line item: documented, budgeted, and under control.
Don’t wait for Q-Day. Start future-proofing your data with quantum-safe security today.

.avif)
